select the best answer. which of the following are breach prevention best practices
High School answered Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your workstation when it is unattendedPromptly retrieve documents containing PHIPHI from the printerAll of this above 1 See answer Add answer 5 pts. Which of the following are breach prevention best practices.

Data Loss Prevention What Is Dlp How Does It Work
Promptly retrieve documents containing PHIPHI from the printer D.

. The following are breach prevention best practices. Are you following best practices for data security and breach prevention. The best way to avoid being a victim of a breach is to prioritize data security.
Convene a workgroup to research threats vulnerabilities. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. Promptly retrieve documents containing PHIPHI from the printer D.
There are Microsoft best practices best practices and practices. Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer Access only the minimum amount of PHIpersonally identifiable information PII necessary Create a strong password policy and enforce it. Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your workstation when it is unattendedPromptly retrieve documents containing PHIPHI from the printerAll of this above.
10 best practices for data breach prevention response plans convene a workgroup to research threats vulnerabilities. What is the best. Which of the following is are breach prevention best practice.
All of this above Best practices for breach prevent are. Best answer 4. Answers is the place to go to get the answers you need and to ask the questions you want.
Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion.
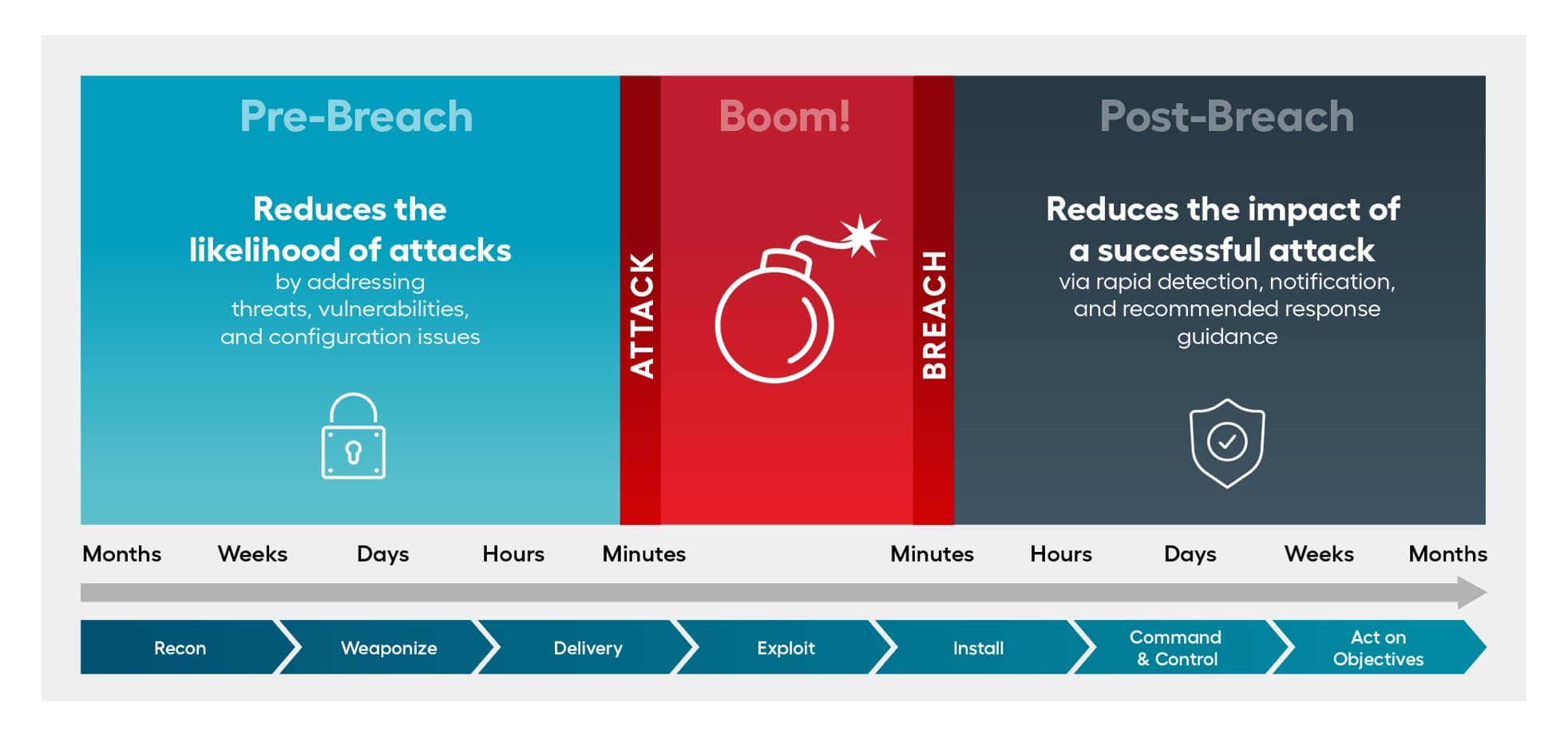
Managed Detection And Response Mdr Solutions Services Alert Logic

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Data Breach Response Times Trends And Tips

Data Loss Prevention Best Practices Endpoint Protector

What Is Intellectual Property Theft And How To Prevent It Ekran System

Data Loss Prevention What Is Dlp How Does It Work

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

10 Secure File Sharing Options Tips And Solutions

Official 2022 Hipaa Compliance Checklist

Official 2022 Hipaa Compliance Checklist

What Is Data Security Definition Planning Policy And Best Practices Toolbox It Security
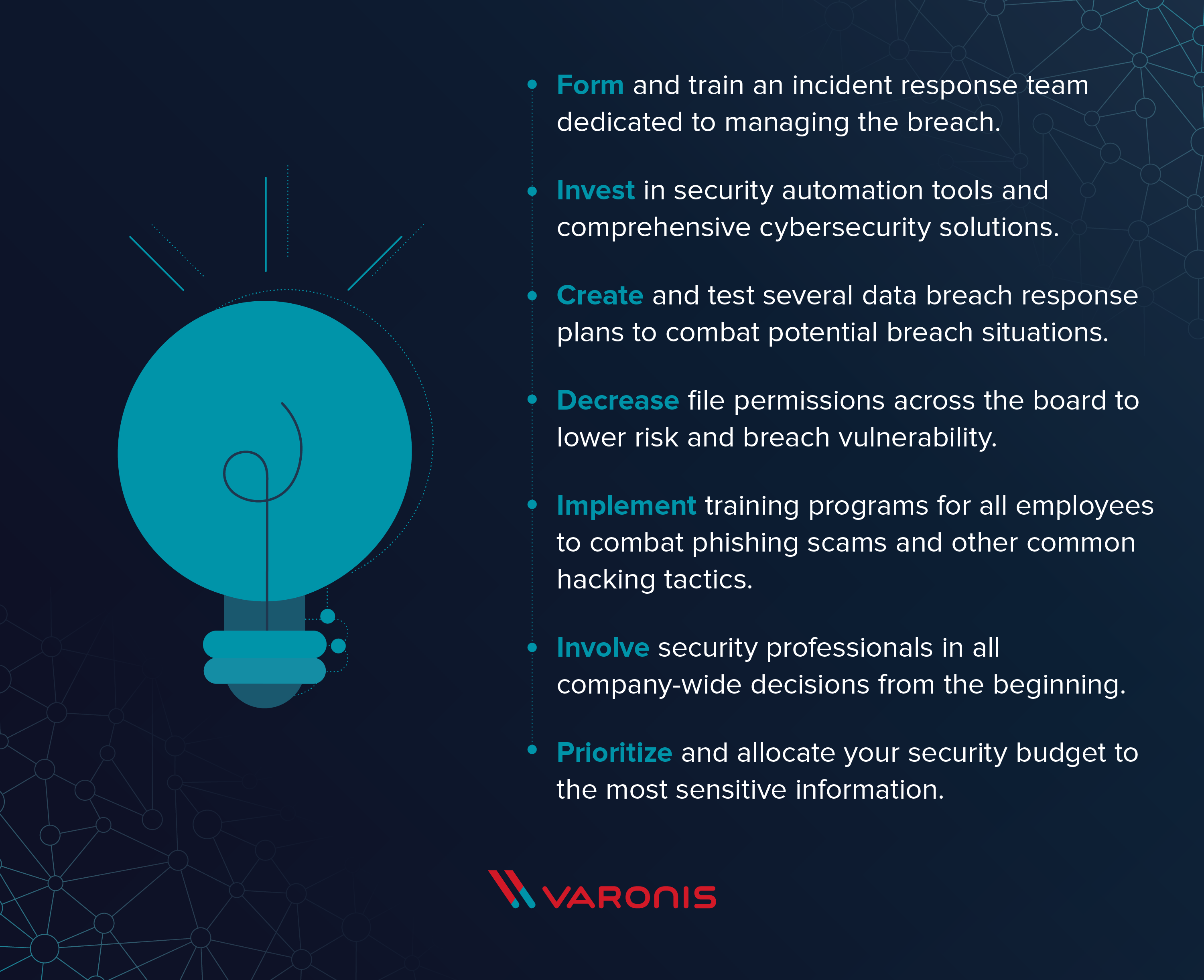
Data Breach Response Times Trends And Tips

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Analyzing Company Reputation After A Data Breach
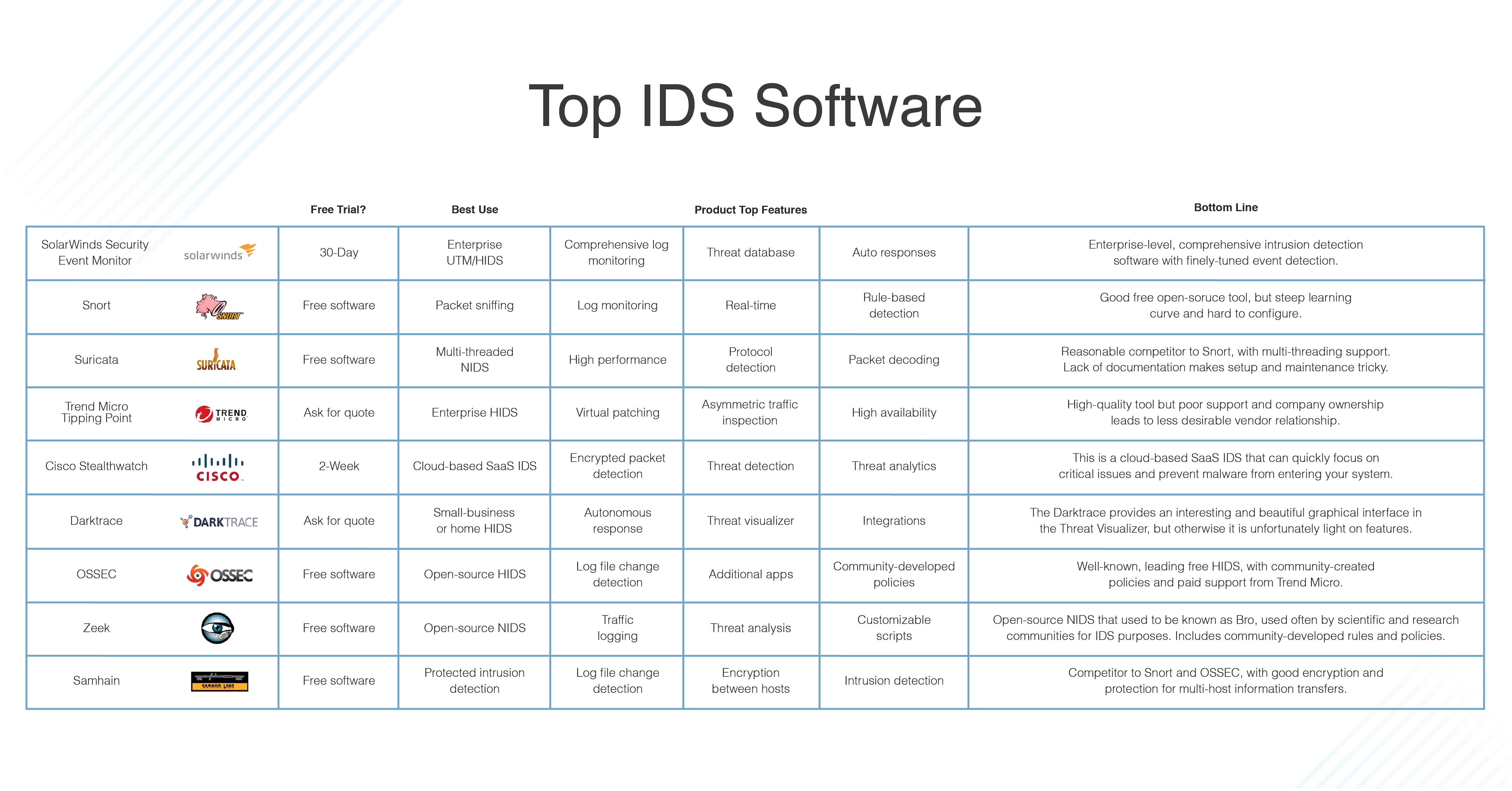
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff

The Ultimate Data Breach Response Plan Securityscorecard

Unauthorized Access 5 Best Practices To Avoid Data Breaches
Frequently Asked Questions About Data Loss Prevention Endpoint Protector